EKOPARTY CTF
Another CTF during in the week - I hate that (I can't participate as much I as want too) but anyway I've took part in this CTF too.
My contribution:
- tasks solved: 2
- points: 150
- time spent: 12h 32m
As stated above I've only managed to solved 2 tasks but actually one of them - web 100 - was quite interesting. It wasn't a difficult one but a lot of people had trouble with them.
Super duper advanced attack
We were give a simple message:
Can you find the flag?
http://0491e9f58d3c2196a6e1943adef9a9ab734ff5c9.ctf.site:20000
The web100 task was a simple webpage that is shown below:
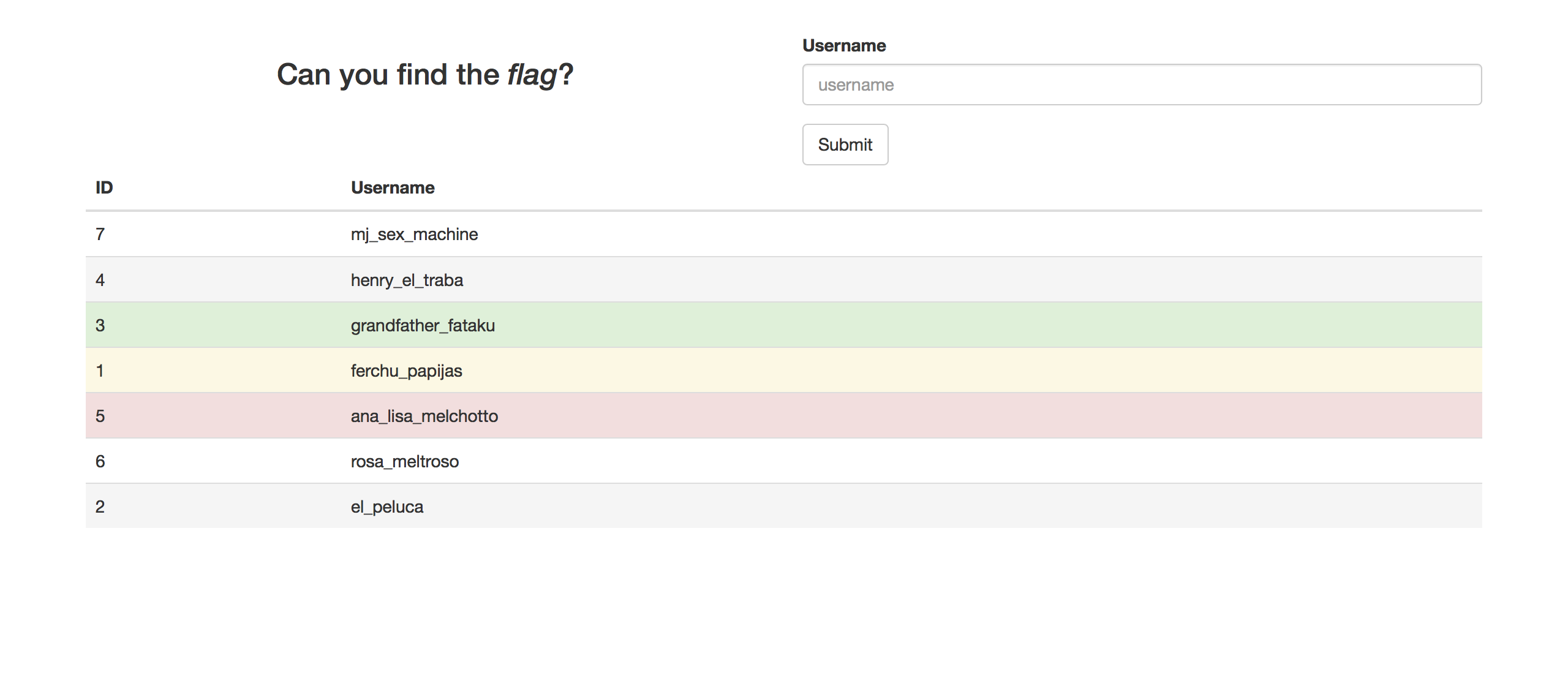
You could very quickly find out that there's an SQL injection in the username field. But the more you look through the objects in the DB the more there was an impression that there is no flag there. And you could leak a lot from the DB. Everything in the users table:
rosa_meltroso'/**/union/**/select/**/username,password/**/from/**/users#
or ENGINES installed in mysql:
rosa_meltroso'/**/union/**/SELECT/**/1,ENGINE/**/FROM/**/INFORMATION_SCHEMA.ENGINES#
or even all the tables and all the columns!
rosa_meltroso'/**/union/**/SELECT/**/table_name,COLUMN_NAME/**/FROM/**/INFORMATION_SCHEMA.COLUMNS#
You could dump all the data but there was no flag! I was going to write a tool that would extract all the values from all the columns but before I went on browsing through the MySQL documentation and came across CURRENT_USER() and started wondering maybe the orgs have returned the flag there but flag() did not work. Executing some standard functions did get me nothing but I've remembered that there are some kind of global variables denoted with @ and started looking the same in mysql. Just to try out I went and executed statement like this:
rosa_meltroso'/**/union/**/SELECT/**/1,@flag#
and surprise, surprise - I got the flag (EKO{do_not_forget_session_variables}). Great!
This task was quite fun and looks like it was a bit of a challenge for people as one could see a lot of requests for a hint.
I think I was 3rd (or somewhere around that) person who solved the challenge.
Later on in the CTF the organizes have revealed a clue:
You don't need to search for the flag outside the DB, there is more than tables and columns in a DB.
and in the end it was solved by 103 teams.
RFC 7230
This web task for 50 points I think is not worth mentioning but for the sake of completeness I will post a one line about it.
All it took to do it was to execute:
curl -v ctf.ekoparty.org
and check the response:
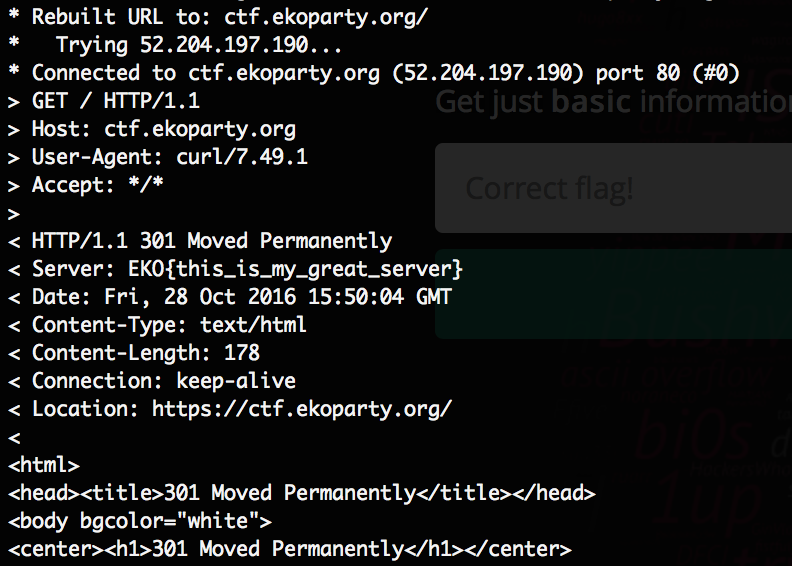
as you can see the flag is there in the Server header. Not the most sophisticated task I must say. Anyway points collected!
Quite nice CTF. Had fun. I just need to solve more tasks next time.
