GynvaelEN - Mission 19 - Solution
Gynvael is back with streams and with missions. The 39th stream contains mission no 19 that can be found here.
In this mission we are given a CHIP-8 ROM image. This is clearly a reference to the latest streams about this topic (#34, #35, #36, #37, #38). If you don't know what Chip-8 is I recommented watching those.
To be able to solve this challenge what we needs is a debugger or at least a decompiler. What my first though was, was to check r2 for a pluging that would support Chip8. Unfortunatelly there was none.
What I found at first was a Chip-8 decompiler. It worked ok, and I got a dissasebly for the crack me.
I've tried analyzing it a bit but gave up pretty quickly as it was to difficult to do manually.
What I need is debugger! And there is one. Written in Go. Chip-8 Emulator.
After downloading it I've loaded the image and was presented with this image.
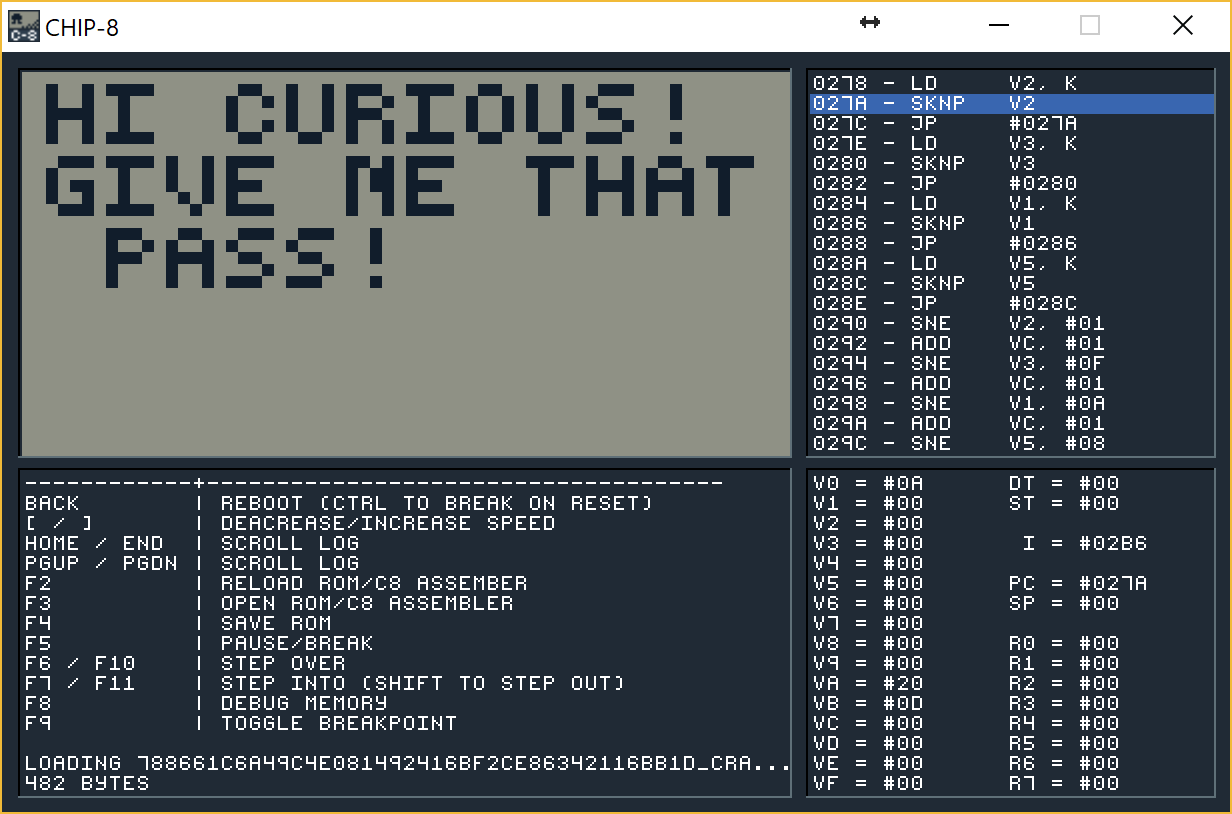
What is good about this tool is that it shows the disassbely as well as the output and registers. Everything what's needed.
If you don't know Chip-8 assembler you can read a bit of intro on the Chip-8 Emulator page. What's needed for this part is to know what does LD Vx,K and SKNP Vx do.
What we see here is that we load keyboard input to V2, V3, V1 and V5. Later (at offset 290) we check those entries with #01, #0F, #0A and #08. If the input is correct we will increment VC register. At first I've tried just typing those as a Pass but it did not work for some reason. Only later I've checked that Chip-8 has it's own keyboard layout that is mapped to a physical keyboard so what we want to press on our keyboard is 1vzs. When we do it viola:
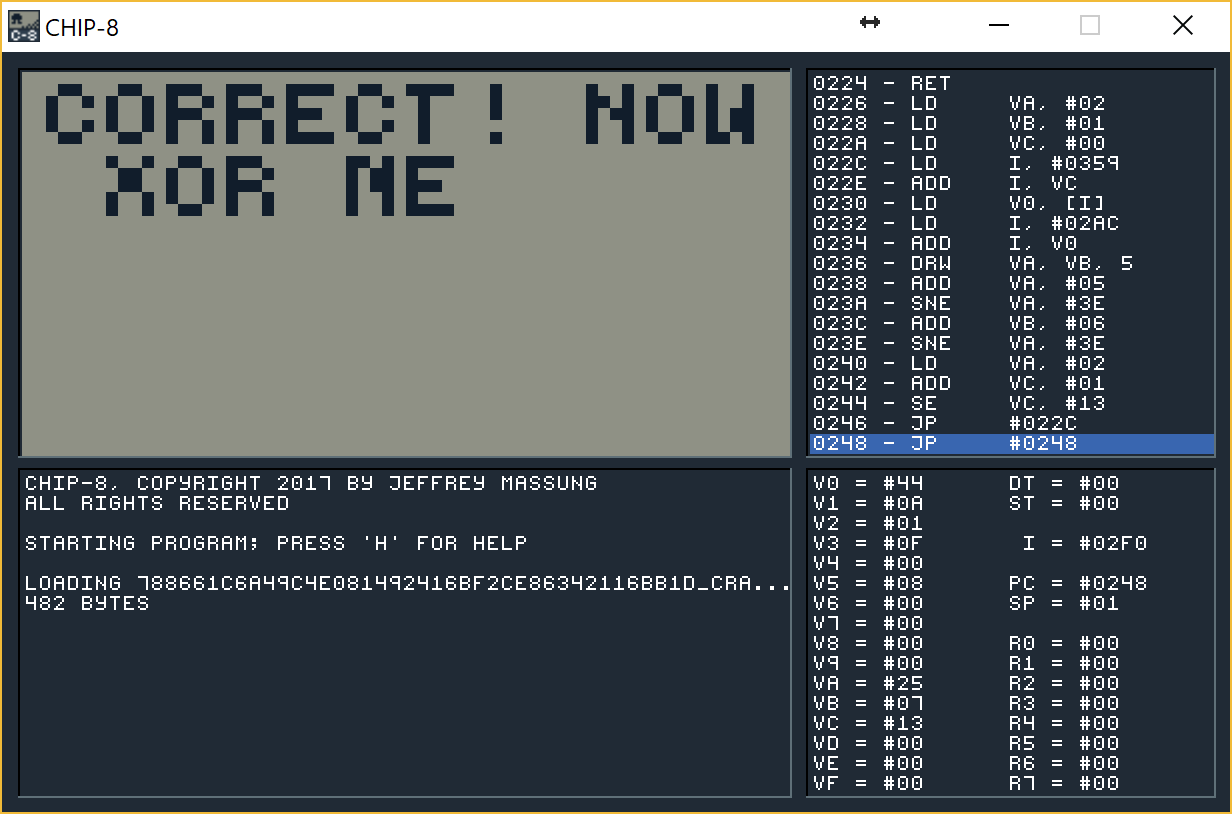
That's interesting. What should we xor? The first assumption was to xor the crackme name (788661c6a49c4e081492416bf2ce86342116bb1d) with they but it did not yield anything. Let's see what was written on the mission page
In the final phase use a string, not a number. Try different offsets.
Hmm, the only way this message is valid would be if we use 1fa8 as the key as this is the valid hex number. Also the offseting might indicate that we have a bit longer data input. Let's try with the whole file data.
Running the script gives us the pass:
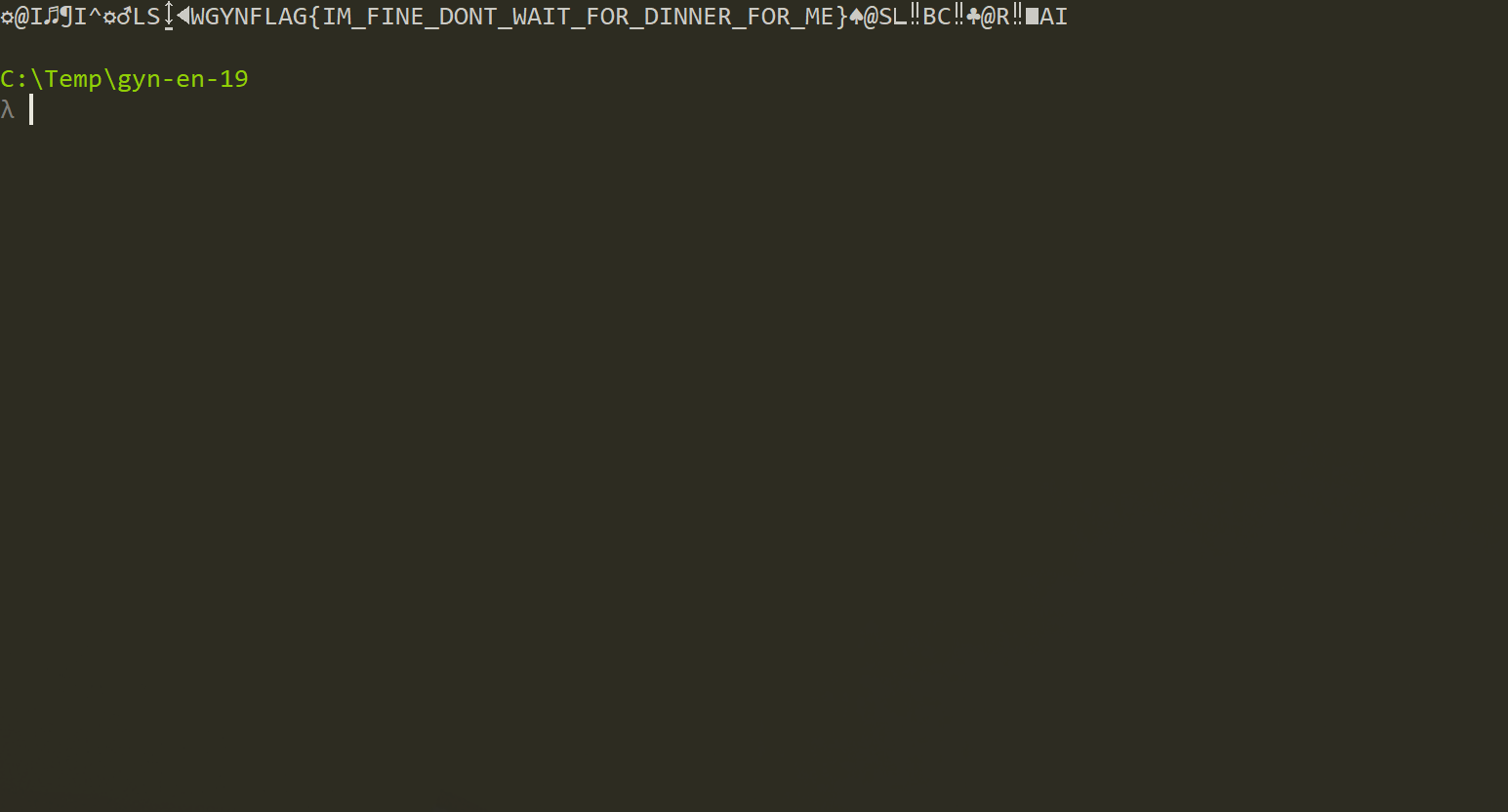
Flag: GYNFLAG{IM_FINE_DONT_WAIT_FOR_DINNER_FOR_ME}.
