Hack.lu 2016

Hack.lu a 24h CTF contest that I was attending after the HitCon. It was challenging for me due to the fact that it was during the week (Wednesday 10:00 UTC - Thursday 10:00 UTC).
Again during this CTF I was playing with the Dragons (Dragon Sector team).
I've attempted to solve two tasks and managed to get the flag for one of them. I've also learnt a lot in terms of how to approach tasks. The team end up on 7th place collecting 1918 points. So it was quite ok I guess. Let's begin.
simple-pdf (PPC 150)
This was quite a large (~30M) pdf file that showed Test123 when you opened it. A closer inspection with peepdf showed that it contained another pdf file inside.
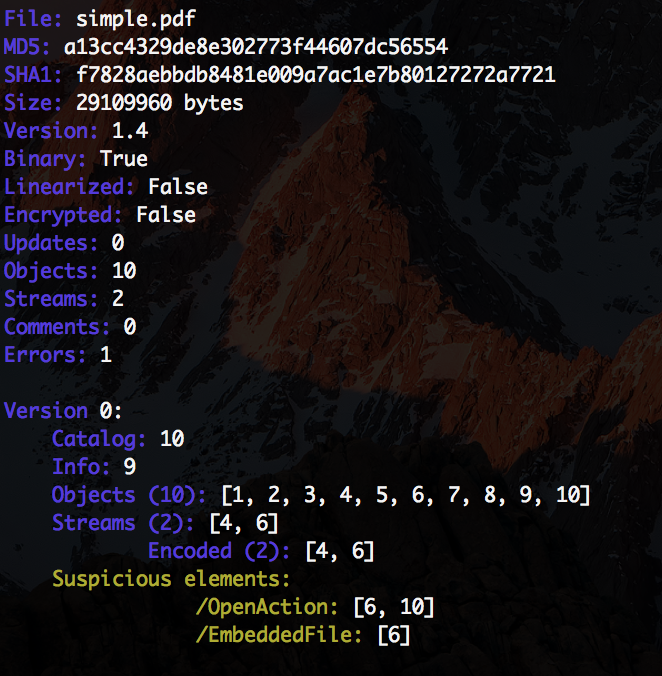
So the first thing I did was to extract the EmbeddedFile with peepdf. The file was a bit smaller then the original one and was also containing an embedded file so I was suspecting a матрёшка (so file inside a file, inside a file and so, so). The metadata of the file suggested there was 10000 iterations so there was no way doing it manually and finishing within the time limit of the CTF. So I took a scripted approach which peepdf supports. By creating a simple script
that will be passed to the tool. A simple execution worked quite well so I put this into the batch file
but there was a problem with such approach as it still took too long to extract a file. I suspect each time peepdf was loading a file it was analyzing it and that was taking the precious seconds. I started working on an in memory extracted to speed things up another team member extracted the last матрёшка-file with a binwalk script using -M option. I didn't even knew that bin walk can do it. Nice...
Lesson learnt: peepdf is a nice tool when you want to analyze a file and learn about its content but due to the analysis phase it's useless to quickly extract content repeatedly. Use the right tool for the job!
More write-ups for this task on GitHub
Cornelius1 (crypto 200)
In this task we were given a server source code
and by quickly examination of it, we can see that the flag is added to the cookie along with user name provided by us and all is returned to us. It is encrypted before doing that of course.
But maybe we can somehow gain the knowledge about the flag? For sure we can. The problem here is that data is compressed before being encrypted and the algorithm that is used is deflate. Why is that bad? Well if we can match data that we pass through the user parameter with the actual flag, we can influence deflate algorithm. It will detect the repeated data in the string and the result will be shorter then if there would be no repetition. We can use this behavior to obtain the flag. By brute-forcing the flag char-by-char we can get it.
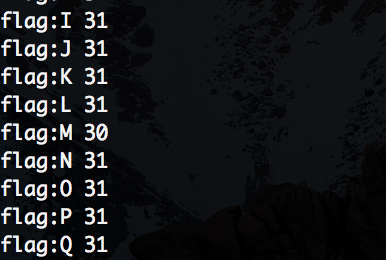
and when we follow the process couple of times we get the full flag
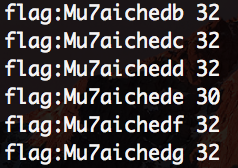
which was: Mu7aichede. Quite a nice task.
More write-ups for this task on GitHub
See you next time!
